RandoriSec was at Hack.lu for its 15th edition and as you can imagine it was super interesting.
In addition this year, RandoriSec sponsored the CTF!
If you’ve never heard of Hack.lu, it’s a 3 days IT security conference held in Luxembourg every year. The conference is attended mostly by cybersecurity professionals from all over the globe. Several subjects are discussed including malware analysis and reversing, forensics, network, mobile and web security and incident response. The program of this year was dense proposing a lot of interesting conferences and workshops and not to forget a final touch with the call of failure which was far away from being a real failure. It was actually a real success and let’s hope it would be in the program for next year.
The list of the conferences is available in YouTube.
Day 1
Smartphone apps: let’s talk about privacy
Axelle Apvrille, reverse engineer and mobile malware researcher, had the honors of starting the event talking about Smartphone apps’ privacy. Axelle wanted to show us the extent of non-respect of privacy by analyzing well known applications such as Instagram, Snapchat or WhatsApp. She first presented the tools she used, like Frida and her own tool DroidLysis, which disassembles android applications and looks for different information in them. For example, the tool searches for patterns of attempts to run an exe, retrieve personal information, etc. She also showed that many of them retrieve information that aren’t relevant to their normal operations.
Fingerpointing False Positives
Desiree Sacher, security architect and SOC analyst, talked about how we can make Security Operation Centers more efficient by preventing false positives, the idea was to make a change to the used security monitoring process and a change in the workflow. The presenter gave some advice about how to optimize the SOC reports also. Desiree published an interesting article on the subject if you want to get further information.
Say Cheese – How I Ransomwared your DSLR Camera
Eyal Itkin, vulnerability researcher, presented his research on DSLR cameras. He first analyzed the firmware of the camera, but it was encrypted, then he had to use a tool called ROM Dumper which is used to update the firmware and while we’re at it analyze its code. Eyal found 5 critical vulnerabilities which allowed code execution and he used it to execute the ransomware that he wrote. A Youtube video showing the attack is available. The full research article is available on the Checkpoint’s website.
Workshops
Several workshops were been held the same day:
- Hacking Bluetooth Low Energy devices with Btlejack by Damien Cauquil
- Reversing Web Assembly by Patrick Ventuzelo
- Introduction to Osquery by David Szili
- Java Web Application secure coding workshop by Eva Szilagy
- Malicious RTF document analysis by Didier Stevens.
Day 2
Sensor & Logic Attack Surface of Driverless Vehicles
The second day started with Zoz, robotic interface designer and researcher. Zoz started the presentation by a quick introduction on cars in general and self-driving cars especially. Zoz covered denial of service and spoofing attacks on:
- GPS
- LIDAR
- Vision cameras/Tesla autopilot
- Millimeter wave radar
- Ultrasonic transducers
- Digital compass
- IMU
- Wheel encoders
- Ground-penetrating radar
Disturbance: on the Sorry State of Cybersecurity and Potential Cures
Saad Kadhi, operational security expert and head of the CERT-EU, compared past, current and possible future trends of the threat landscape. Very interesting to checkout on this link.
Leveraging KVM as a debugging platform
Mathieu, security researcher, presented VM introspection on KVM then showed how to setup KVM-VMI, integrate in LibVMI and then use KVM as a debugging platform. An interesting approach when playing with sandboxes and malware analysis.
Fileless Malware Infection and Linux Process Injection in Linux OS
Hendrik Adrian, malware researcher, presented how the exploitation with fileless method is also affecting Linux. Then, he showed some new methods of fileless infections and their usage in some public incidents.
DeTT&CT: Mapping your Blue Team to MITRE ATT&CK
Rouben Bouman and Marcus Bakker, IT Security Professionals, presented the DeTT&CT framework build atop of MITRE ATT&CK, that helps blue teams to gain insight into these aspects and to start prioritizing their defense efforts. The ultimate goal of DeTT&CT is to become more resilient against attacks targeting organizations. They show how they improve their threat hunt using the following steps:
Data Source > Visibility > Detection > TTP’s
Then, they presented the DeTT&CT framework they developed to administrate, score and compare data sources quality, visibility detection and behaviors.

Workshops
Several workshops were been held the same day:
- Repacking the unpacker: Applying Time Travel Debugging to malware analysis by Benoit Sevens
- Faup workshop, parse and investigate URLs! By Sebastien Tricaud
- Hash collisions exploitations by Ange Albertini
- Sigma Workshop by Thomas Patzke
- Understanding and exploiting buffer overflows by Antonin Beaujeant
- Learn to use ONYPHE to have a view on your Internet exposed devices by Patrice Auffret
The second day finished with 5 min talks per speaker and the call for failure.
Day 3
Who contains the containers
Loana Andrada and Emilien Le Jamtel, security professionals, presented most common vulnerabilities such as CVE-2019-5736
which lead to runC container breakout.
They also showed unsecure configurations found on container technologies and how to exploit them.
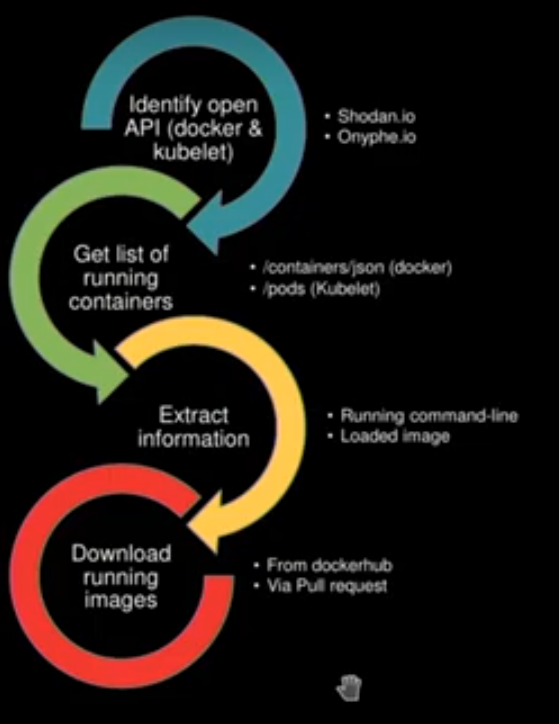
Finally, they showed how easy it is to find compromised containers on the Internet:
Defeating Bluetooth Low Energy 5 PRNG for fun and jamming
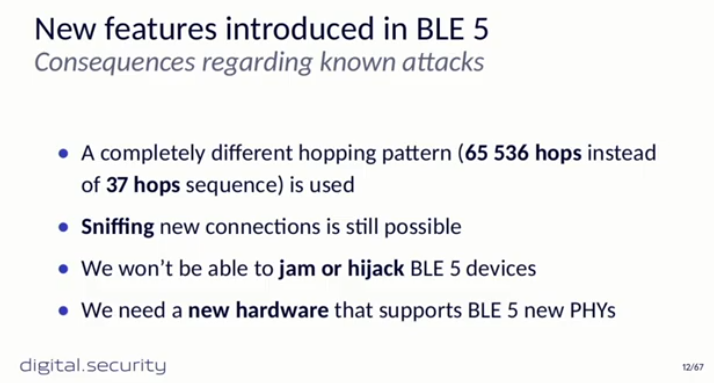
Damien Cauquil, security professional and researcher, explained BLE 5 and known attacks of previous version of it (4.2 and before) like sniffing,
jamming and hijacking. Then, he talked about new features introduced in BLE 5.
DNS On Fire
Paul Rascagneres and Warren Mercer, security researchers, presented how DNS work, they then explained DNS redirect attacks and showed several examples and finally they talked about the attack campaign DNSpionage in which threat actors create a remote administrative tool that supports HTTP and DNS communication with the attackers’ command and control(C2). More information on the subject on this link.
Workshops
Several workshops were been held the same day:
- Snarf it! Firmware extraction and analysis with open source tools by Pauline
- IOCs are dead, long live the IOCs! by Celine Massompierre
- Junior CTF Install Party by Axelle Apvrille
- Practical Incident Response, With Automation and Collaboration Inside by Saad Kadhi
- Intro to Dark Arts: Getting Started with CTFs by Shruti Dixit, Geethna TK and Sowmya
- Introduction to WHIDS an Open Source Endpoint Detection System for Windows by Quentin Jerome
The last day was closed off with CTF prizes distributions.


