RandoriSec was at the Amsterdam 2018 edition of Hack In The Box and… IT WAS A BLAST !
It has been over a month and many tweets, write-ups and even the full slides (https://conference.hitb.org/hitbsecconf2018ams/materials/) have been published so we won’t cover details here but we just wanted to say a few words about it.
The agenda was great with two main conference tracks, one dedicated track for the labs and one additional, free and open to public, track:

Brida: When Burp Suite Meets Frida - Federico Dotta and Piergiovanni Cipolloni
We particularly liked the “Brida” presentation because it introduced a very nice Burp Suite extension that let you play with Frida. Very handy when it comes to assess the security of mobile applications !
Slides and video are here:
https://conference.hitb.org/hitbsecconf2018ams/sessions/brida-when-burp-suite-meets-frida/
And you can find Brida extension here:
https://github.com/federicodotta/Brida
From Zero to ARM Assembly Bind Shellcode - Azeria
We did this very interesting lab where, starting from zero, you finally get an ARM shellcode (and a reverse one too) at the end of the 2 hours thanks to an incredible trainer: Azeria.
Video doesn’t seem to be available but you can find a VM to train and a lot of materials on her website:
GSEC Lucky draw
How can you encourage people waking up early after a heavy social event ? With a lucky draw !
Well it worked for us and we won the famous PoC||GTFO book :)
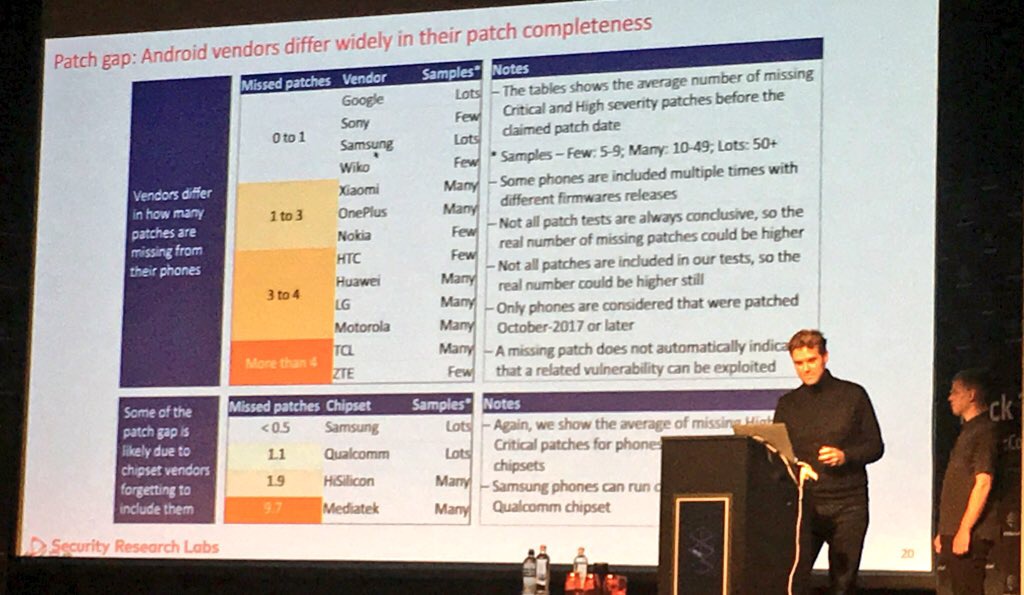
Mind the Gap: Uncovering the Android Patch Gap Through Binary-Only Patch Level Analysis - Karsten Nohl and Jakob Lell
Android patch management is a mess. Users have to rely on phone vendors to install security fixes and some are not doing their job correctly. Really.
This conference presented the research they did on analysing hundreds on patches with a signature based approach.
They also unveil the v2 of SnoopSnitch, a mobile app they did to detect missing security fixes, even on non rooted Android phones.
Slides and video:
SnoopSnitch:
https://play.google.com/store/apps/details?id=de.srlabs.snoopsnitch&hl=en